Toady, we are releasing multiple new versions of Icinga 2 and Icinga for Windows, all of them fixing a file permission issue present in all installations on Windows. Impact The following paths were...
Releasing Icinga 2 v2.15.2, v2.14.8, v2.13.14 and Icinga for Windows v1.13.4, v1.12.4, v1.11.2
Toady, we are releasing multiple new versions of Icinga 2 and Icinga for Windows, all of them fixing a file permission issue present in all installations on Windows. Impact The following paths were...

Integrating Prometheus Metrics into Icinga Using check_prometheus
Introduction This article explains how to integrate metrics from Prometheus into Icinga checks using the check_prometheus plugin. There can be multiple reasons why this could be desired: Maybe you have different teams with their own monitoring systems, and you need to...

Testing Icinga in a Homelab Setup With Nextcloud
If you want to get started with Icinga but don’t have a data center lying around, no worries. Icinga is a lightweight monitoring tool that works for both large infrastructures and small home labs. When I first explored Icinga during my first year as an apprentice, it...
Icinga Insiders: Collaborating With Users to Improve Icinga Web
Icinga Insiders: How User Research Shapes the Future of Icinga Web Icinga Insiders is one of our core initiatives for involving users directly in the ongoing development of Icinga Web, its modules, and new functionality. Through structured research sessions, we gain...
Releasing Icinga DB v1.5.1
Today we are announcing the release of Icinga DB version 1.5.1. This release addresses the issue of leaking SQL prepared statements when Icinga DB is configured as a source for Icinga Notifications. Each time the custom variables for an Icinga Notifications event were...
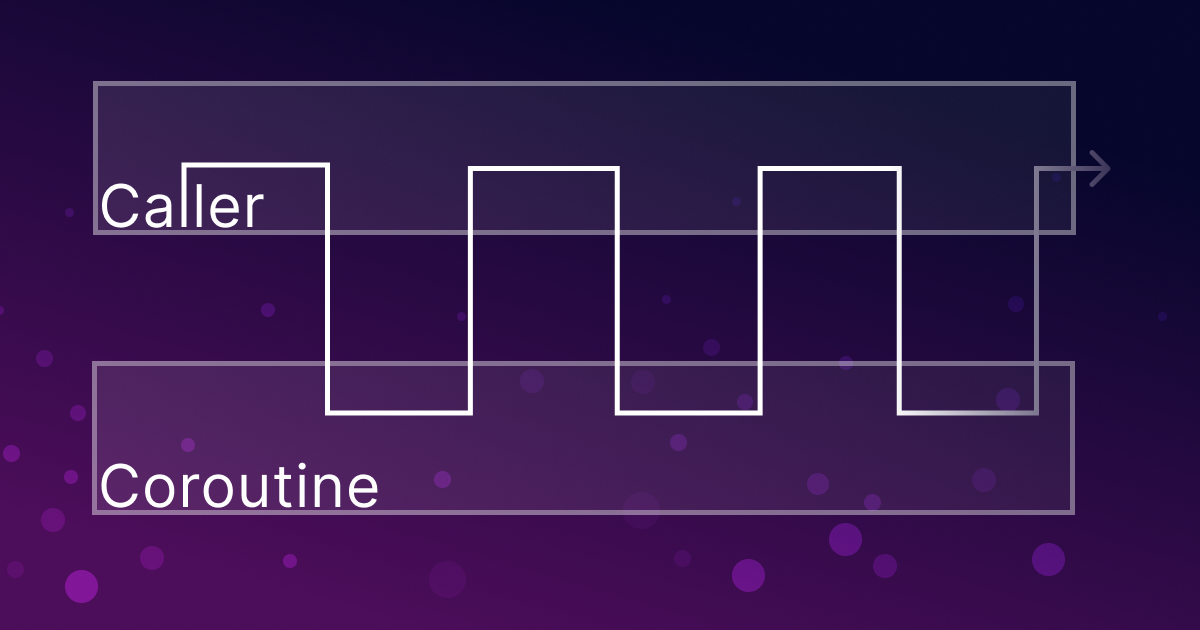
Exploring C++20 Coroutines: A Practical Look at Stackless Coroutines vs Boost.Coroutine2
Introduction Icinga 2 makes heavy use of Boost.Coroutine2 in our network code, which are stackful coroutines that are designed to work well with the IO operations from Boost.Asio. This has proven to be a challenge whenever we wanted to asynchronously await things...
Monitor One Icinga 2 Cluster From Another
Icinga is designed to be a highly dynamic monitoring software that can monitor your setup, regardless of its architecture. While most setups are hierarchical and fit well into the master, satellites, and agents scheme with different zones, it is sometimes impractical...
Drowning in Alert Fatigue? How to Regain Control of Your Monitoring
Introduction: Why Alert Fatigue Hits Sysadmins Sooner or Later If you’ve ever muted your phone during a maintenance window, only to miss a real outage an hour later, you’re not alone. Sysadmins on Reddit and beyond often describe feeling like they’re drowning in...
How to Fix Cyclic Inheritance Errors in Icinga Director during Object Configuration
Icinga Director is a powerful tool that greatly simplifies the configuration, management, and deployment of monitoring objects in Icinga. It provides a user-friendly interface and automation features that make complex setups easier to maintain. Occasionally, though,...
Ipl-html: Introducing new Form Element Decorators
A Fresh Take on Form Element Decorators Decorators have always been a powerful concept in Icinga Web’s form system — letting developers control how form elements are displayed without hardcoding markup everywhere. But until recently, the decorator system had its...
Icinga Notifications v0.2.0 Release
Some of you might have already heard about this at OSMC, or you may have received a release notification from GitHub already: our Icinga Notifications project made a step forward and we are happy to announce that version 0.2.0 is now available for you to try out. It...
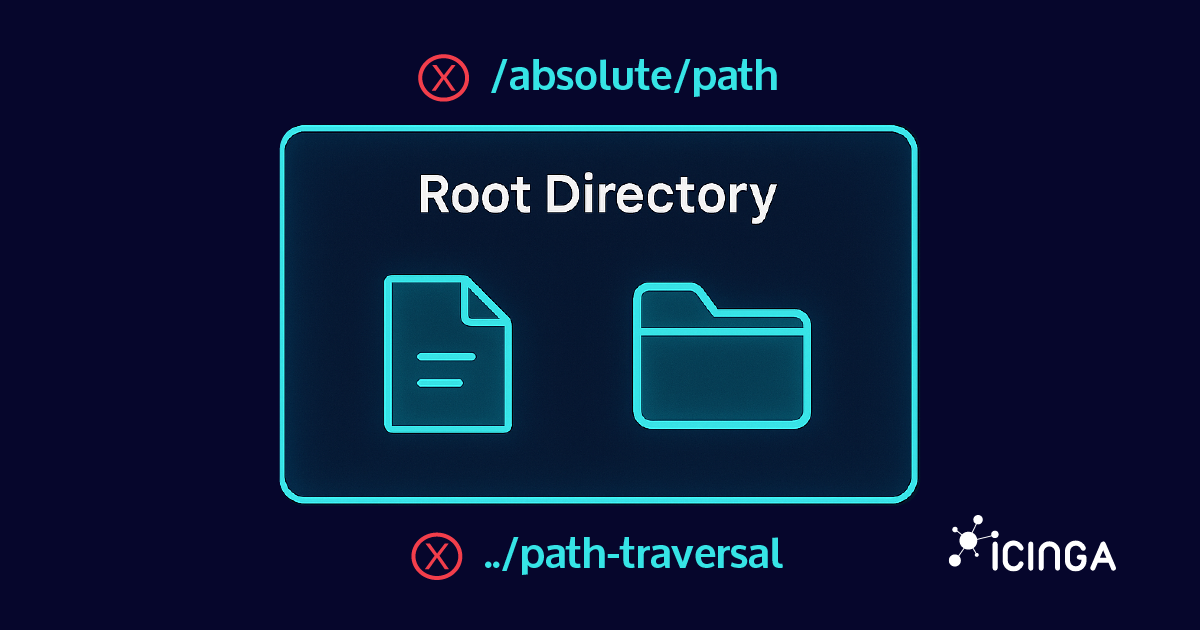
Secure File Operations in Go with os.Root: Preventing Path Traversal
Go's os.Root feature, introduced in Go 1.24, is designed to improve filesystem security by restricting operations to a specific directory, making it much harder for attackers to exploit path traversal vulnerabilities. This is especially valuable for scenarios like...

Subscribe to our Newsletter
A monthly digest of the latest Icinga news, releases, articles and community topics.