Why wait for the next poll? An SNMP trap is a real-time alert sent from a device to a monitoring system, without waiting for polling.
Ever had a router die silently at 3 AM while your monitoring system was still polling away every 5 minutes? Yeah… not fun. That’s where SNMP traps step in.
Think of them as the push notifications of network monitoring: instant, lightweight, and sometimes misunderstood. Let’s break down what SNMP traps are, why they matter, and how you can use them effectively.
What Is an SNMP Trap?
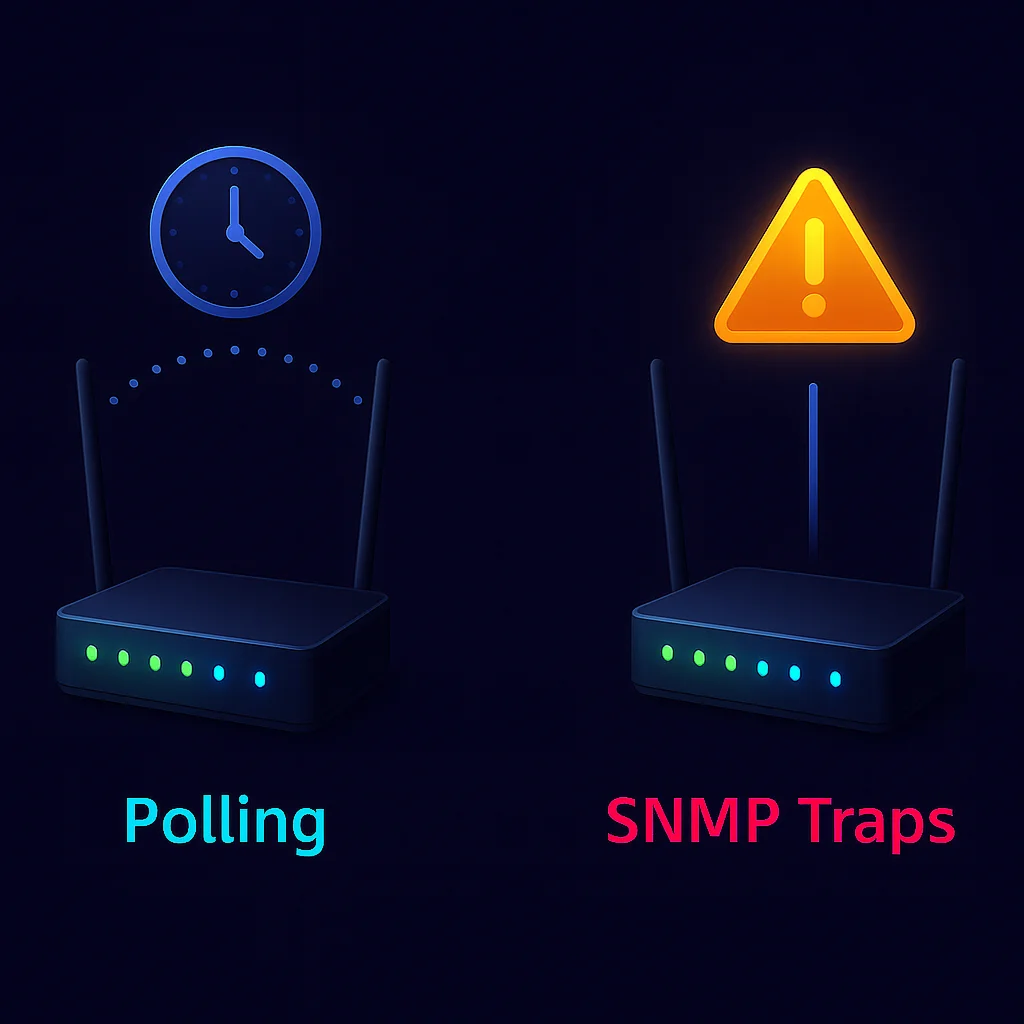
Before we look at the benefits, let’s start with the basics. If polling is about asking devices how they’re doing, traps flip that around: the device tells you when something’s wrong, right when it happens.
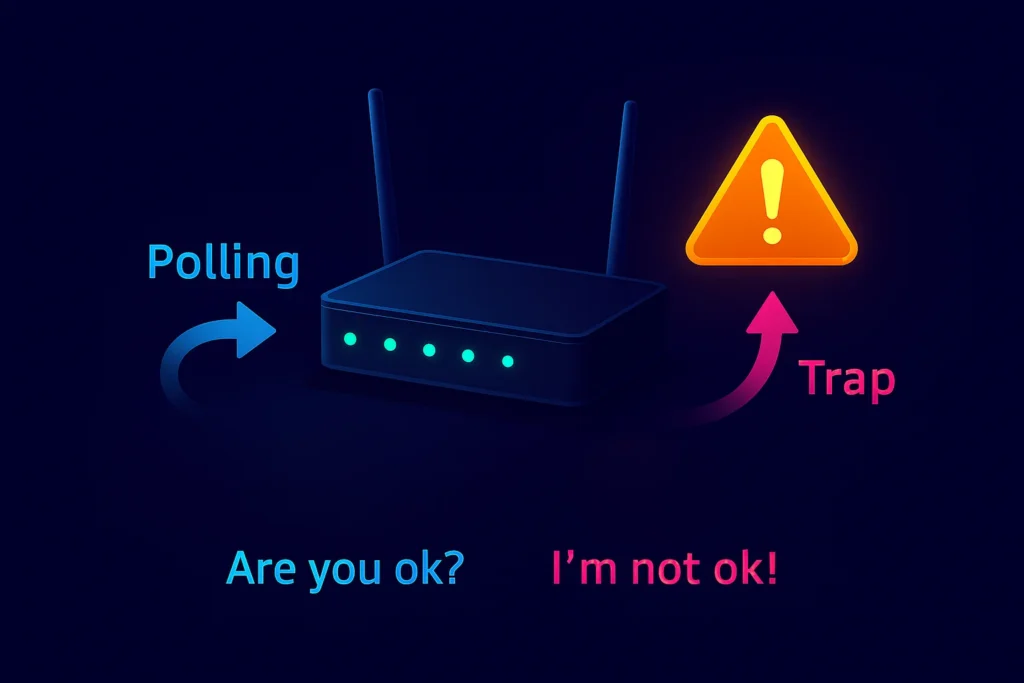
At its core, an SNMP trap is an unsolicited alert: a little “Hey, attention needed!” ping from a network device straight to your monitoring system.
SNMP traps are asynchronous Protocol Data Units (also called asynchronous messages) sent by the SNMP agent on a device to an SNMP trap receiver whenever something important happens. Examples include a router overheating or an interface going down.
Unlike polling, traps do not wait for a manager to request the status. They bypass polling entirely. The device simply sends the alert as soon as the issue occurs.
TL;DR: Polling asks “are you ok?” every few minutes, while traps yell “I’m not ok!” the second trouble hits.
Why SNMP Traps Matter
So why bother with traps when you already have polling in place? Because speed and precision matter. Polling is reliable, but it’s also slow and blind in the gaps between cycles.
-
Real-time alerts: No waiting for the next polling cycle. You know instantly.
-
Efficient and targeted: Small and lightweight, with context encoded via Object Identifiers (OIDs) from the Management Information Base (MIB).
-
Beyond polling: Polling loops might miss the moment a device starts overheating. Traps catch it in real time.
Example: If you poll every 5 minutes, the worst-case detection time for an outage is 4:59 later. With traps, you know the second it happens.
Types of SNMP Traps Explained
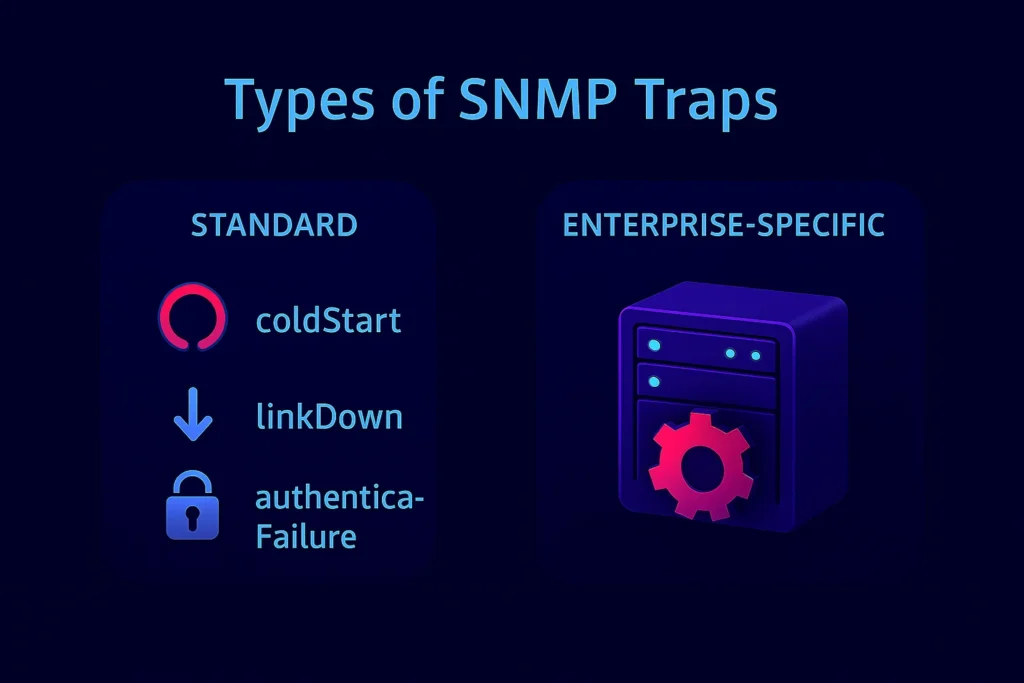
Not all traps are the same. Some are universal, others are tailored to specific hardware or vendors. Knowing the difference helps you set expectations and interpret alerts correctly.
- Generic (standard) traps: Defined in RFC 1215, such as coldStart, linkDown, or authenticationFailure.
- Enterprise-specific traps: Vendor-defined alerts tailored to device-specific events. These require the correct MIB to interpret them properly.
Note: Traps exist in all SNMP versions (v1, v2c, v3), though security and reliability differ. SNMPv3 is recommended for environments where authentication and encryption matter.
SNMP Trap Receiver: The Middleman You Need
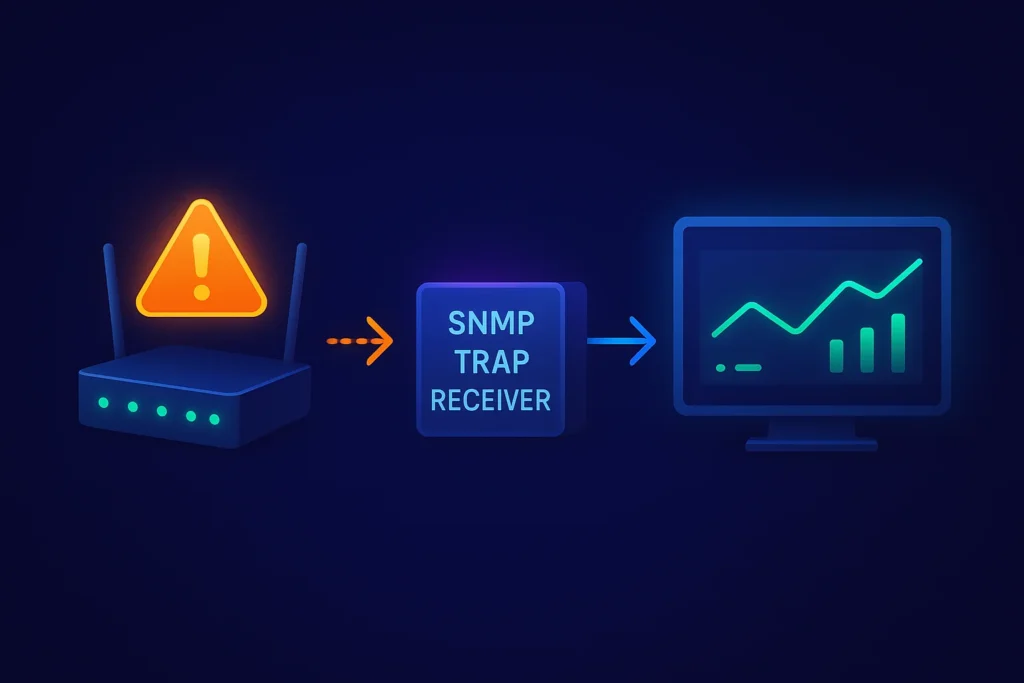
Before we get into the downsides of traps, it’s important to know how they even reach your monitoring system. Devices don’t talk directly to your monitoring tool, they need a listener in between.
That’s the job of an SNMP trap receiver (also called a client or listener). It sits on port 162, waits for traps, and translates them into something your monitoring stack can understand.
The most common tool is snmptrapd from the Net-SNMP suite, which can log traps, filter them, or forward them further into your monitoring or alerting system.
For more readable output, many setups add a translator such as SNMPTT (SNMP Trap Translator). It converts raw OIDs into clear text messages using MIBs, making it easier for humans (and your monitoring software) to make sense of the alerts.
Without a receiver and often without a translator, traps never make it past your devices in a useful way. Think of it as the translator between raw SNMP chatter and actionable alerts.
Common Pitfalls of SNMP Traps
Traps sound amazing, but they’re not bulletproof. They come with quirks, limitations, and gotchas that you need to be aware of if you don’t want to be left in the dark.
-
UDP = no delivery guarantee: Since traps use UDP, they might get lost in transit. No retransmissions, no acknowledgments.
-
Your tool chain still matters: Even with a receiver in place, you need to configure it and your monitoring setup properly, so traps get decoded and processed as intended.
-
When devices crash, silence reigns: If a device dies completely, it won’t be able to send a trap. That’s why traps should complement, not replace, polling.
- Check firewalls and ports: If traps aren’t arriving, make sure UDP port 162 is open on both the sender and the receiver. Firewalls or SELinux rules often block SNMP traffic by default.
- Verify MIB availability: If traps show up as raw OIDs instead of readable text, the right MIB file may be missing. Import the vendor’s MIB into your monitoring setup (e.g., SNMPTT) to translate OIDs into human-readable alerts.
Best Practices for SNMP Trap Monitoring
To really get the most out of traps, it’s not enough to just enable them. You need a strategy: balance them with polling, fine-tune what you collect, and make sure your team is ready to handle them.
-
Mix traps and polling: Use traps for immediate awareness of critical events, and polling for regular health checks.
-
Consider informs: SNMPv2 “inform” messages add reliability by requiring acknowledgment and retrying if needed.
- Secure your traps: If possible, use SNMPv3 or secure the channel, since SNMPv1/v2c traps are sent in clear text.
-
Filter at the source: Configure devices to only send the traps you care about. Otherwise, you’ll drown in noise.
-
Train your team: Understanding OIDs, decoding trap data, and reacting properly are skills that need practice.
SNMP Traps in a Nutshell
Traps aren’t here to replace polling, but to strengthen it. Together, they give you both the broad visibility of scheduled checks and the instant awareness of real-time alerts. Use them thoughtfully, balance them with polling, and make sure your team knows how to handle them – that’s how you stay ahead of outages. Think of polling as your regular doctor checkup and traps as your body screaming when you stub your toe. You need both if you want to stay healthy.
Used alongside polling, SNMP traps are an essential part of modern monitoring. Learn more about how Icinga helps you monitor networks efficiently and in real time.
SNMP Traps FAQ
What is an SNMP trap in simple terms?
An SNMP trap is a real-time alert from a device to your monitoring system. Instead of waiting to be asked (“polled”), the device shouts immediately when something goes wrong.
Do SNMP traps replace polling?
No SNMP traps don't replace polling. Traps are great for instant alerts, but if a device completely crashes it can’t send anything. Polling is still needed to verify ongoing health and catch silent failures.
Which SNMP versions support traps?
All SNMP versions support traps (v1, v2c, v3). SNMPv3 is generally preferred today since it adds authentication and encryption, which older versions lack.
What do OIDs and MIBs have to do with traps?
Traps use Object Identifiers (OIDs) to encode details about the event. A Management Information Base (MIB) is like a dictionary that translates those OIDs into human-readable text.
How are SNMP traps received and processed?
Devices send traps to a receiver listening on UDP port 162. A common setup uses snmptrapd to capture them and a translator such as SNMPTT to turn raw OIDs into readable alerts.
Are SNMP traps reliable?
They use UDP, so delivery isn’t guaranteed. If you need extra reliability, consider using SNMPv2 “informs”, which require acknowledgment.