Introduction
“Please enter the code we just sent you.” – most people have seen this message when logging into an online service. Two-Factor Authentication (2FA) is no longer reserved for banks or enterprises. It’s now common in email, social media, and shopping accounts.
The idea is simple: in addition to a password, you need a second factor so that attackers can’t break in with just one piece of information. But what methods are actually used – and how secure are they really?
At Icinga, we also recognize the importance of stronger authentication. That’s why we’re actively working on a 2FA solution to make monitoring environments more secure and resilient.
2FA in Detail – Methods and How They Work
There are several ways to implement a second factor, each with its own strengths and weaknesses.
The most familiar method for many users is the one-time code sent by SMS or email. After entering a password, a message arrives with a short numerical code that must be typed in to complete the login. It’s simple and convenient, since it doesn’t require additional apps or devices. But this simplicity comes at a cost: SMS can be intercepted through SIM swapping, and email accounts are often less secure than the services they’re meant to protect.
A more advanced and widely used option is the time-based one-time password (TOTP), generated by apps like Google Authenticator or Authy. When you link your account, a secret key is shared between the service and your app via a QR code. Both then use this key to generate codes that refresh every 30 seconds. This approach avoids the weaknesses of SMS and works offline, but it has its own flaw: the server must store that secret, often in plain text. If an attacker gains access to the database, they can recreate the codes themselves.
Some services rely on push notifications instead. When you log in, a prompt appears on your phone asking you to confirm. One tap, and you’re in — no typing required. This method improves user experience but introduces another vulnerability: attackers can abuse it by spamming victims with repeated login prompts until they accept one out of annoyance, a tactic known as MFA bombing.
Finally, there are hardware security keys such as YubiKeys or other FIDO2-compatible tokens. These small USB or NFC devices are considered the gold standard of authentication. Instead of codes, they use cryptographic operations tied to the legitimate domain of the service, making them resistant to phishing. The trade-off is that they’re less convenient for casual users and require a small upfront investment.
The Weaknesses – Why 2FA Isn’t Unbreakable
Two-Factor Authentication makes accounts significantly harder to break into, but it’s not an impenetrable shield. Attackers have adapted, and several methods allow them to bypass or exploit 2FA protections.
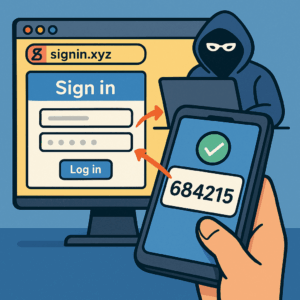
Another frequent issue arises with push-based authentication. While convenient, it has led to what’s known as “MFA bombing” or “push fatigue.” Attackers repeatedly trigger login attempts, bombarding the victim with approval requests until the person, out of frustration or confusion, finally taps “Approve.” This simple form of social engineering has already been used successfully in high-profile breaches.
Some weaknesses are more technical. SMS-based authentication can be defeated through SIM swapping, where criminals use social engineering to convince a mobile carrier employee to transfer a victim’s phone number to a new SIM card. Once that happens, the attacker receives all text messages — including 2FA codes.
Even TOTP (time-based one-time passwords), often seen as more secure, has its own blind spot. To generate the same codes as the authenticator app, the server must store a shared secret. In many cases, this secret is kept in plain text in the database. If attackers gain access, they can simply generate valid codes themselves without needing the victim’s phone at all.
Finally, there are attacks that sidestep authentication entirely. Malware or session hijacking can steal cookies and tokens from an already logged-in browser. In such cases, 2FA doesn’t even come into play, because the attacker takes over an existing session rather than trying to log in from scratch.
All of this doesn’t mean 2FA is pointless — far from it. It stops the vast majority of opportunistic attacks and remains one of the most effective protections you can enable. But it’s important to recognize that “two factors” does not mean “absolute security.”
Passkeys – The Future Beyond 2FA
Passkeys are a new way of logging into online accounts without using traditional passwords. They’re built on open standards like FIDO2 and WebAuthn, developed by the FIDO Alliance together with companies like Apple, Google, and Microsoft.
Instead of remembering a password, you prove your identity with a cryptographic key pair:
-
Private key: Stays securely on your device (e.g., phone, laptop, or hardware security key). It never leaves the device.
-
Public key: Stored by the online service when you register.
When you log in, the service challenges your device. The private key signs this challenge, and the service checks it against your stored public key. If they match, you’re in.
Why this matters:
-
Phishing-resistant: Your private key can’t be tricked into authenticating on a fake website – it only works with the real domain.
-
No shared secrets: Unlike TOTP or SMS codes, there’s nothing in the server database that attackers can use to generate codes.
-
User-friendly: Logging in feels like unlocking your phone – Face ID, fingerprint, or a simple device PIN.
-
Cross-platform: Passkeys can sync across devices via secure cloud services (iCloud Keychain, Google Password Manager, etc.).
In short: Passkeys replace passwords with something stronger, easier, and resistant to most common attacks.
Conclusion
Two-Factor Authentication is essential today. It protects against password theft, credential stuffing, and many low-effort attacks. But it’s not bulletproof: real-time phishing, SIM swapping, push fatigue, and weak storage of TOTP secrets all show its limits.
In the short term: Everyone should enable 2FA – preferably with strong methods like app-based codes or hardware tokens, not just SMS.
In the long term: Passkeys are paving the way toward a passwordless future that’s both safer and easier to use.
Soon, we might not be asking: “Two factors, double security?”
Instead, we may be asking: “Do we even need passwords anymore?”