Have you ever admired those cool graphics on the web? They look nice but can be the wolf in sheep’s clothing. In this post you will learn about SVG injections and how to avoid them.
What is SVG?
Before we get into the topic of SVG injection, let’s understand SVG itself. Scalable Vector Graphics is a popular graphic format, allowing images to scale without losing quality. It’s the go-to choice for dynamic visuals, bringing a touch of magic to our digital canvases. SVG can also be used to display data graphically or add animated elements. If you want to learn more about this, I recommend the blog post by Jan Schuppik about the potential of SVGs.
SVG Injection
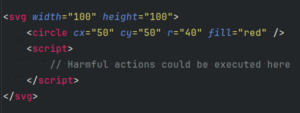
Let’s now turn to a critical consideration. Allowing users to upload SVGs to a website can be a tricky step that brings potential threats into your home. SVGs, while visually appealing, can harbor hidden dangers in the form of malicious scripts. It’s like welcoming a guest without fully understanding their intentions – a risky proposition. This practice opens the door to security vulnerabilities, so it is crucial to exercise caution and take strict measures when handling SVG uploads to prevent the inadvertent inclusion of malicious scripts.
SVG Uploads: Quick Security Tips
To reduce the risk of uploading SVG files that contain malicious scripts, it’s important to implement strict security measures. We recommend thoroughly validating and sanitizing any uploaded SVG files. Additionally, we suggest implementing server-side checks to verify the integrity of the file’s structure, ensuring it adheres to the expected SVG format. Finally, we recommend applying file type validation to confirm that only legitimate SVG files are accepted. To keep your website secure, it’s important to use content inspection tools to scan for potential embedded scripts or suspicious patterns within the SVG content. Additionally, it’s recommended to restrict the allowed SVG elements and attributes to a predefined whitelist to reduce the potential for harmful injections. It is also crucial to ensure that your server-side validation routines are regularly updated to adapt to emerging threats. Lastly, it’s important to educate users on the importance of uploading only trusted SVG files. Alternatively, it is of course always possible to completely deactivate the upload of SVGs. By following these measures, you can greatly improve your defense against harmful scripts embedded in SVG files.
Conclusion
In conclusion, as developers, it’s vital that we are proactive in securing our web applications against SVG injections. By implementing recommended measures we can strengthen our defenses.
In my role as a developer, I’m committed to integrating these security practices into my workflow. It’s not just about creating visually appealing websites, it’s also about ensuring that they are resilient to potential threats. Let’s prioritize both exceptional user experiences and the security of our digital platforms, and guard against the dangers hidden in the allure of SVG graphics.